How To Install Brutus On Ubuntu Linux
Ready to test a number of password brute forcing tools? Password's are often the weakest link in any system.
Give your machine a name. Personally I think it is a good idea to go for the Linux distribution name (i.e. Ubuntu) and the version number (14.04, 15.04, 15. Graphics Design Book In Bangla Free Download. 10 etc). Select “Linux” as the type and “Ubuntu” as the version. Make sure you choose the correct version based on whether you have a 32-bit or 64-bit machine. Click “Next” to continue. 'How to install Brutus' is not written yet. Download File List. Category: Software, People, PersonalForge, Magazine, Wiki. OpenSource Downloads. 1, FFFTP (29,379). 2, CrystalDiskInfo (14,220). 3, CrystalDiskMark (6,506). 4, 7-Zip (5,034). 5, Android-x86 (4,370). 6, Clonezilla (3,503). 7, Tera Term (2,900).
Testing for weak passwords is an important part of security vulnerability assessments. I am going to focus on tools that allow remote service brute forcing. These are typically Internet facing services that are accessible from anywhere in the world. Another type of password is attacks against the password hash, using tools such as a powerful tool that is able to crack encrypted password hashes on a local system.
The three tools I will assess are, and (from nmap.org). Installation of all three tools was straight forward on Linux. Use the standard method to compile an application from source. Wget./configure make make install wget./configure make make install wget./configure make make install Then I grabbed a list of 500 passwords from. Of course you can find password lists with many thousands or even millions of passwords. You will need to chose what is the most appropriate for your password testing as factors such as target type and rate of testing will be major factors. Wget The following tests were performed against a Linux Virtual Machine running on Virtualbox.
Speed will vary depending on whether the target is local, the latency of the connection and even the processing power of the target system. Heavy brute forcing can impact a targets CPU potentially causing a condition.
Take care if testing production systems. The first series of tests was against SSH. I set the root account with the password toor. I added toor to the end of the 500 password list at number 499. ~# hydra -l root -P 500-worst-passwords.txt 10.10.10.10 ssh Hydra v6.3 (c) 2011 by van Hauser / THC and David Maciejak - use allowed only for legal purposes. Hydra (starting at 2011-05-05 16:45:19 [DATA] 16 tasks, 1 servers, 500 login tries (l:1/p:500), ~31 tries per task [DATA] attacking service ssh on port 22 [STATUS] 185.00 tries/min, 185 tries in 00:01h, 315 todo in 00:02h [STATUS] 183.00 tries/min, 366 tries in 00:02h, 134 todo in 00:01h [22][ssh] host: 10.10.10.10 login: root password: toor [STATUS] attack finished for 10.10.10.10 (waiting for children to finish) Hydra (finished at 2011-05-05 16:48:08 Successfully found the password with Hydra!
Hi i am having problem ‘make’ing ncrack i get the following errors at the end. As i am new to linux, i don’t understand the error? Any ideas Compiling modules cd modules && make make[1]: Entering directory `/home/Dave/ncrack-0.4ALPHA/ncrack-0.4ALPHA/modules’ g++ -c -I. I am having a problem on ‘make install’ of medusa plz help ” make install Making install in src make[1]: Entering directory `/home/user/Desktop/medusa/medusa-2.1.1/src’ Making install in modsrc make[2]: Entering directory `/home/user/Desktop/medusa/medusa-2.1.1/src/modsrc’ make[3]: Entering directory `/home/user/Desktop/medusa/medusa-2.1.1/src/modsrc’ make[3]: Nothing to be done for `install-exec-am’.
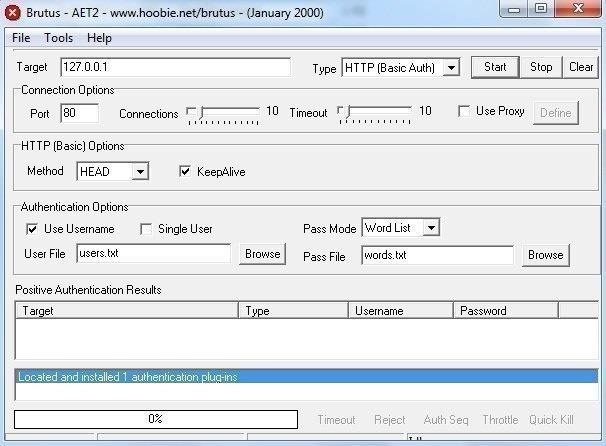
If you don’t know, Brutus Password Cracker is one of the fastest, most flexible remote password crackers you can get your hands on – it’s also free to download Brutus. It is available for Windows 9x, NT and 2000, there is no UN*X version available although it is a possibility at some point in the future. Brutus was first made publicly available in October 1998 and since that time there have been at least 70,000 downloads and over 1.6 Million visitors to this page. Development continues so new releases will be available in the near future. What is Brutus Password Cracker For? In cryptanalysis and computer security, password cracking is the process of recovering passwords from data that have been stored in or transmitted by a computer system. A common approach (brute-force attack) is to try guesses repeatedly for the password and check them against an available cryptographic hash of the password.
Brutus was written originally to help me check routers etc. For default and common passwords. Features Brutus version AET2 is the current release and includes the following authentication types: • HTTP (Basic Authentication) • HTTP (HTML Form/CGI) • POP3 • FTP • SMB • Telnet Other types such as IMAP, NNTP, NetBus etc are freely downloadable from this site and simply imported into your copy of Brutus. You can create your own types or use other peoples.
I tried to download Brutus from hobbie.net (the master image)and Avast found a Trojan in the.zip file: So much for wanting to try a software that suppose to crack passwords “ Hack to learn” is the motto, eh? Nice “touch” inserting a trojan into the zip file just to fuck up with people’s computers, eh.darknet? Good thing Avast rocks and douche bags like you are stopped every now and then. Oh, by the way. Specify in the stupid box with “please add 5 and 8” or whatever numbers that what the system requires is not to just write those numbers in the box, but requires a mathematical operation Who said that all the hackers are smart?
Marie, You will notice that your previos message was deleted by the moderators as you were asking for advice as to how to perform an illegal act. I sympathise with your situation but breaking the law will not help you. As you have little knowledge of Information Security, etc, you would get caught and I’m sure you and your daughter would not benefit from that. If you are concerned with what your daughter is doing online, might I suggest that you monitor her activities, physically, by locating your computer into a shared area in your house. There are other methods which will fall into greyer areas of the law depending on ownership of the computer system, the country you are in, the age of your daughter, etc. I apologise if I am coming across as a bit preachy but there is no substitute for proper parenting.
Well, thanks for that gem of wisdom there hikup. I’d agree with grav there too – even if you sit behind an fortress doing brute attacks, you’re going to get seen by someone. Maybe not the people who are meant to be the network admin on the sites or servers being bruted – but someone is going to see that traffic, and they’ll certainly be taking all kinds of interests in you or at the least, your own hardware / network / etc. I think brutes are best used – in testing, cause you need to account for the possibility of someone else (or their botnet) using such methods, and not-online brutes, eg – decrypting a drive or some such that you have actually with you. Which is also of course, why they are legit apps also. The best way to get a password – or for that matter any personal information is social engineering.
A system can be impenetrable, but there is always one flaw, and that is the human element. Social engineers run the most risks (there is no proxy string to hide behind) but in the long run, they are the ones that get the most out of anything with the least amount of actual “hacking” A really good example is with the “hacking” of Paris Hilton’s SideKick. The ppl who stole all of her photos and stuff were pretty much hacking amateurs, but they were able to convince one of the T-Mobile personnel to give them the correct access codes and such to allow them to pull off the “heist” Its the same thing with brute forcing, either you can try to brute force a website or ftp server or whatever, or with a quick phone call, you can find out everything you wanted to find out.